Apple’s standard data-safety practices, along with its new ultra-secure protection option, come with some risk if you forget your Apple ID password. Here’s what to do if that happens.
It might happen to us all at some point: you’ll simply get confused about which password was for what and enter the wrong one for your Apple ID too many times, or perhaps someone else is attempting to access your Apple ID account. Suddenly you can’t access Apple’s myriad services, or your iCloud, and you’re not sure what to do.
For most users, the solution is pretty simple:
- On another device, head to the website https://iforgot.apple.com
- Enter your Apple ID email address.
- You’ll be told to check your other devices for a verification code in either the form of a text message or an email.
- Enter the verification code on the website.
- You can now enter a new, unique Apple ID password, and confirm it.
Apple will then text you a message with a six-digit recovery code to your previously-verified cellular phone number. This does not need to be an iPhone or Android phone, but it must be able to receive SMS text messages.
Depending on the preference you chose when setting up your Apple ID account, Apple may instead send an email with the code. If you accidentally chose your own Apple email account — @icloud.com, @me.com, or @mac.com — as the recovery email, this of course won’t work and you’ll have to contact Apple directly for further assistance.
For those who chose a “landline” home phone or non-cellular number to receive the code when setting up their Apple ID, Apple will still (as of this writing) call and have a robot voice tell you the recovery code. Apple is one of the last big tech companies to continue offering this method, and this service could disappear in years to come — so be sure once the account is recovered to update the method by which you want to receive any future recovery codes.
Once the new password is confirmed, you’ll need to sign back in on all your devices to re-enable Apple and iCloud services. As part and parcel of the iCloud service, Apple encrypts some 14 types of user data both in transit and stored, and this is now referred to as Standard Data Protection.
Some items under Standard Data Protection are fully end-to-end encrypted (E2EE), meaning Apple doesn’t have the ability to decrypt those items — only authenticated users with trusted devices can do so. Health data, passwords stored in iCloud Keychain, payment information, and destinations in Apple Maps are examples of the kinds of iCloud user data Apple doesn’t have access to.
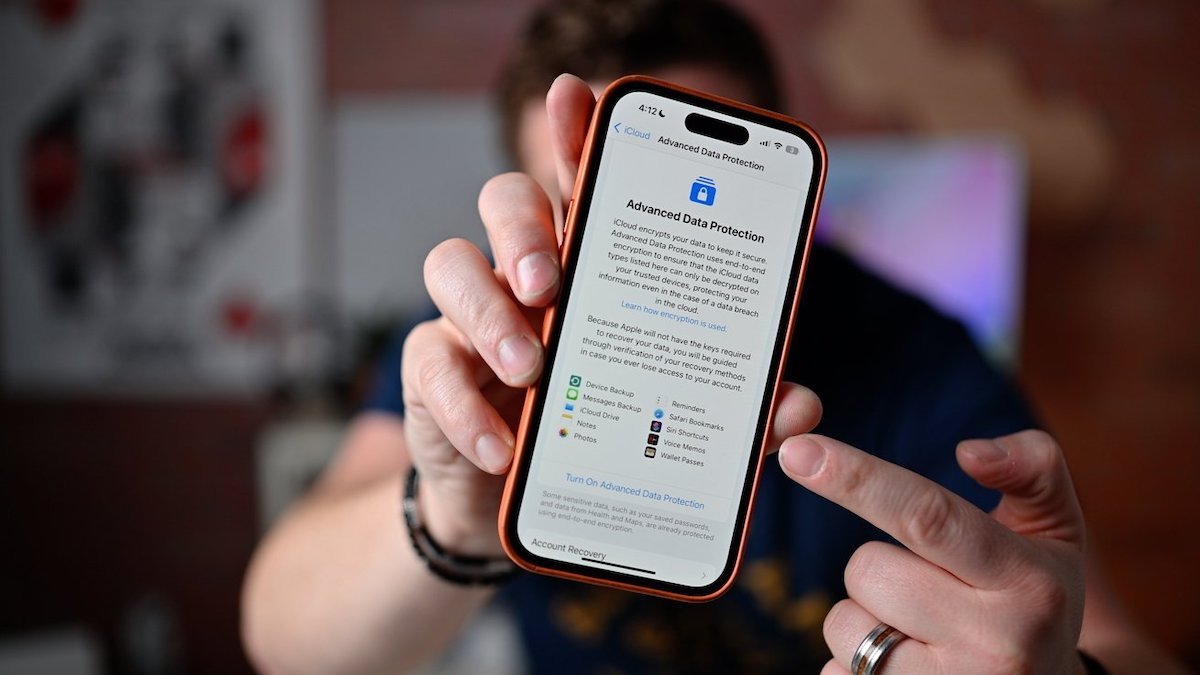
A new layer: Advanced Data Protection
With the release of iOS 16.2, PadOS 16.2, and macOS Ventura 13.1, Apple has added a new option for users: an additional layer of security for material stored on iCloud called Advanced Data Protection (ADP). It further E2EE encrypts parts of the data users sync or store on iCloud, and more importantly makes the user and their trusted devices — rather than Apple — responsible for handling the decryption.
We’ve already written about how to choose this option, and some of the caveats that go with that. ADP is intended as an optional feature for those who think they have data stored on or backed up to iCloud that makes them a target for surveillance or hacking.
If you do turn on ADP, your iCloud backups, along with additional categories of stored data are now end-to-end encrypted — but not everything has decryption keys that only you control. Because of the need to be universally interoperative with other systems, iCloud Mail, your Contacts, and your Calendars are not part of Advanced Data Protection.
These items are still encrypted both “in transit” through the internet as well as while “at rest” on the iCloud servers, but Apple retains those decryption keys for compatibility purposes.
Some of the key concepts behind Advanced Data Protection were introduced in 2020 with iCloud Data Recovery Service. It debuted the idea of setting up a Recovery Contact — a trusted person other than you that could help you recover your Apple ID — and also featured the option of setting up a Recovery Key that Apple doesn’t have access to.
As of iOS 16.3, Apple has also now added support for third-party physical security keys, which resemble USB thumb drives to allow users to verify themselves, skipping the usual “verification code” stage. For ADP recovery, Apple requires users have two security keys — one presumably stored in a safe place — to prevent being permanently locked out in case of the keys is lost or malfunctions.
It is also worth noting that turning on ADP makes the collaboration features in many Apple apps more difficult or problematic. By default, access to iCloud.com through a web browser is disabled when ADP is turned on. Users can authorize a one-hour window to iCloud.com from a trusted device, and this temporarily makes access to the website available to that trusted device only.
Collaboration features in areas like shared Notes, iCloud Shared Photo Library, or shared Reminders won’t work if you have ADP turned on unless all your collaborators also have ADP turned on, according to Apple. Shared Albums in Photos are not eligible for ADP protection, and instead use Standard Data Protection.
Likewise, collaboration features in the iWork apps like Pages, Numbers, and Keynote don’t support Advanced Data Protection. When a user opens a shared document in those apps or from an iCloud shared folder, the encryption keys for that document are sent to Apple’s servers in order to coordinate the document changes between participants.
There’s yet another caveat: turning on ADP means committing to keeping all of your Apple devices — iPhones, iPads, Apple TV, Macs, and Apple Watch — fully up-to-date. If you have devices that can’t be upgraded to 16.2 or later, they can’t be used to assist you if you get locked out.
Higher protection, but also higher risk
If you think you are now or will someday be at risk of losing/forgetting two of your most important passwords as Apple device users — your passcode and/or your Apple ID password — you may want to avoid turning on Advanced Data Protection. The biggest risk is that if you lose access to your fallback methods of verification, Apple can’t help you get back in: it is possible to be permanently locked out of your account.
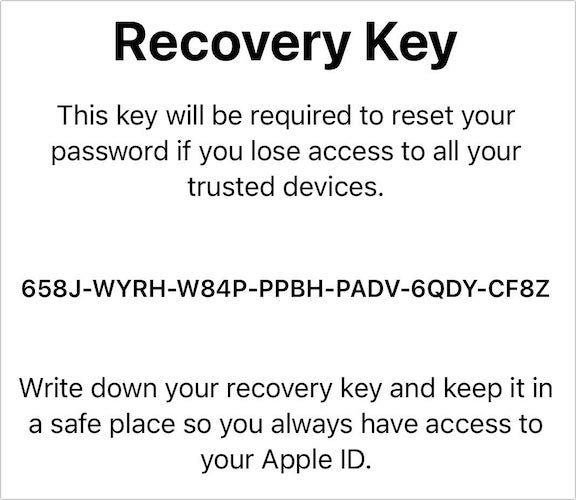
Of course, Apple doesn’t want that to happen — but the fundamental idea behind ADP is that in exchange for this additional encryption, Apple will no longer have the ability to decrypt the protected data, even if served with a warrant. When setting ADP up, Apple can generate a unique 28-character Recovery Key that users can store, and also encourages users to designate trusted others as account recovery contacts.
However, both of these methods could fail over time — a recovery contact changes their contact information, for example, or you can’t find the record of your recovery key. Trying to change your Apple ID password in the usual way described previously will not work if ADP is active.
Because of this, Apple requires that the users using ADP set up at least one alternative recovery method, and encourages users to list multiple recovery contacts. Users should also store at least one printed copy of the “recovery key” in a disaster-proof safe place, such as a bank deposit box.
After some testing, we recommend you set up at least one recovery contact before opting to also get a recovery key. As happens throughout the process, Apple will repeatedly warn you of the importance of keeping recovery contacts up-to-date, and not losing the recovery key.
In setting up a recovery key, the generated key will be shown to you with an option to print it out, and then you’ll be asked to verify the key by either pasting it in, or typing it in. Once the recovery key method is active, you can go back and also add other recovery contacts if desired.
Recovering your Apple ID under ADP
With ADP set up and active, your devices should continue to work as they always do, with users logging in using a passcode (iPhone, iPad) or password (Mac) on their trusted devices. Periodically, or when signing in to the App Store to make a purchase — even if the item is free — you will need to confirm your Apple ID password as you have in the past and it all should go as expected.
However, if you repeatedly mistype or forget your Apple ID password, the rescue operation will be considerably different than for those who don’t have ADP turned on, as enumerated above. Apple has not yet detailed the complete ADP recovery procedure, but it is similar to the procedure used by the iCloud Data Recovery Service.
if you fail to unlock your Apple ID password and the account is locked, the recovery web page will ask first if you would like to recover your account by inputting the recovery key previously created. This is why Apple encourages users to print out and safely store the recovery key.
It is important, if you choose this route, to very carefully input the 28-digit key. It is not currently known how many attempts you will get to successfully input the key, but it will not be many — and could be as little as a single attempt.
Should this method fail, any recovery contacts you previously stored will be offered for you to choose from. The person previously designated will receive a text or email message from Apple with a validation code they must report to you within a short time window.
You will then enter the relayed verification code, whereupon you will be taken to the usual Apple ID password reset page where you will create and confirm a new, strong Apple ID password. As usual, all your other devices will need to sign in again to the Apple ID using the new password.
Once that’s done, the E2EE information stored on iCloud will again be accessible and decrypted on demand from your devices as before. Remember to revisit and update your recovery contacts’ information periodically to ensure that Apple can reach them if they are ever needed again.
This story originally appeared on Appleinsider